LDAP-login on Debian 11/12
April 12th 2022
The goal
The goal is to be able to login with your Active Directory credentials on a Debian machine.
Only members of the DEB-SRV-Users group and local users are going to be able to login.
Installing prerequisites
apt update
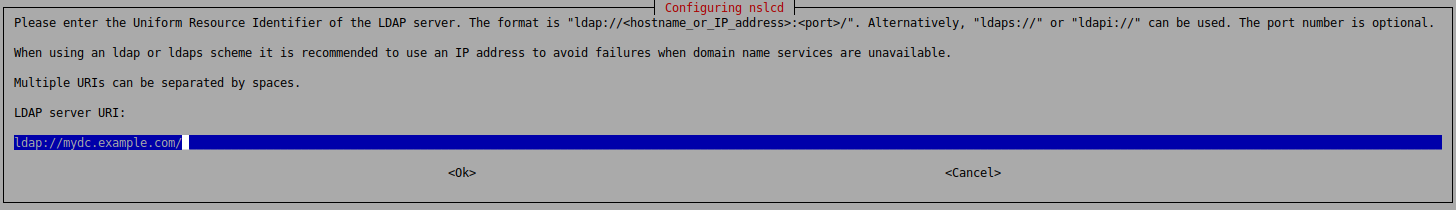
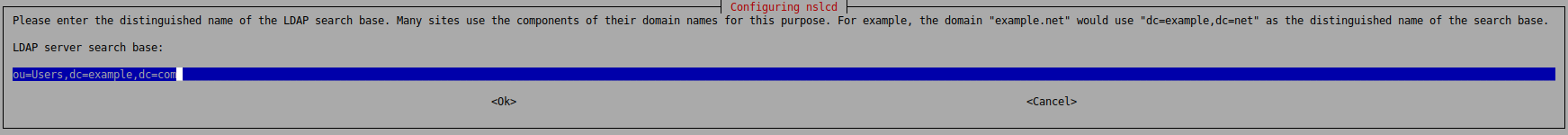
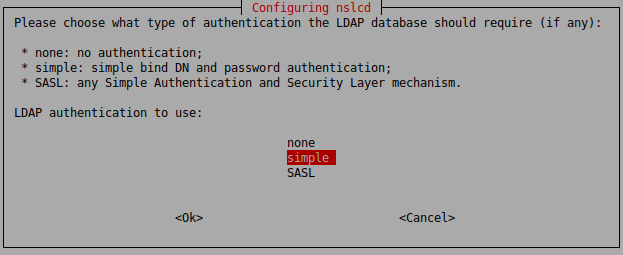
apt install libpam-ldapdWhile installing the libpam-ldapd package you will get a series of prompts:
 Afterwards you will be prompted for the DistinguishedName and Password of the bind user.
Afterwards you will be prompted for the DistinguishedName and Password of the bind user.
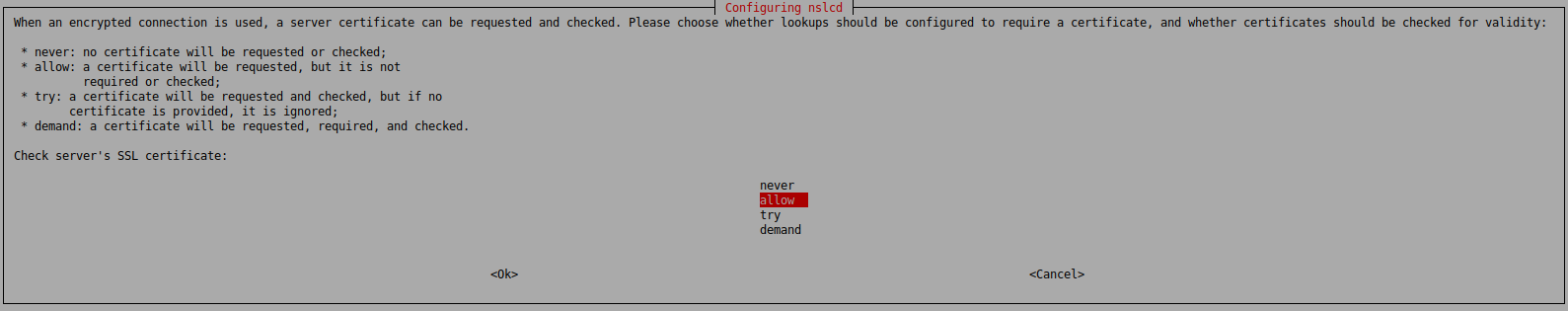
In case you want to rerun those prompts you can just reconfigure the nslcd package:
dpkg-reconfigure nslcdConfiguration
/etc/nsswitch.conf
Add ldap to the passwd, group and shadow lines
passwd: files systemd ldap
group: files systemd ldap
shadow: files ldapDomain-SID
To get the domain-SID you just need to run Get-ADDomain on a domain-joined machine with RSAT. We will need it in the next step.
...
DomainSID : S-1-5-21-2222483658-6132663573-3907530145
.../etc/nslcd.conf
# The user and group nslcd should run as.
uid nslcd
gid nslcd
# The location at which the LDAP server(s) should be reachable.
uri ldap://your-ldap-server.company.com/
# The search base that will be used for all queries.
base ou=Users,dc=company,dc=com
# Mapping user attributes to AD attributes
map passwd uid sAMAccountName
map passwd gidNumber primaryGroupID
map passwd homeDirectory "/home/$sAMAccountName"
map passwd gecos displayName
map passwd loginShell "/bin/bash"
map passwd uidNumber objectSid:<DOMAIN-SID-HERE>
# only allow users in the DEB-SRV-Users Group
filter passwd (&(objectClass=user)(memberof=CN=DEB-SRV-Users,OU=Groups,DC=example,DC=com))
# The LDAP protocol version to use.
ldap_version 3
# The DN to bind with for normal lookups.
binddn CN=MyBindUser,OU=Users,DC=example,DC=com
bindpw BindUserPassword
# The DN used for password modifications by root.
#rootpwmoddn cn=admin,dc=example,dc=com
# SSL options
ssl start_tls
tls_reqcert allow
tls_cacertfile /etc/ssl/certs/ca-certificates.crtSSL / LDAPs
If you want to use an encrypted connection to the LDAP-Server, you have to have
either a CA-Certificate (you can export it using certlm.msc on Windows) or
the LDAP server's certificate. You can get it via this command on Linux:
openssl s_client -connect YOUR-LDAP-SERVER:636 -showcerts </dev/null 2>/dev/null | openssl x509 -outform pemSave the certificate to /etc/ssl/certs/your-ca-cert.crt for example and change tls_cacertfile accordingly.
/etc/pam.d/common-session
We need to create a home directory whenever a new users logs on for the first time.
To do this we only need to add the following line to /etc/pam.d/common-session
session optional pam_mkhomedir.so skel=/etc/skel umask=077Finishing up
Restart nscd and nslcs service
systemctl restart nscd.service nslcd.serviceAfter that you should already be able to login with AD users.
Troubleshooting
In case something does not work you can always
- check
/var/log/auth.log - Run nslcd in foreground:
systemctl stop nslcd nslcd -d